rocknowbot
Should Docker Run -net=host Work?
Docker Run Image
I am running a (QNAP) NAS with Docker functionality ('). I thought it would be a lot safer to install apps via containers instead of apps from the store (or 3rd party stores).
Many packages are outdated in their official store and QNAP runs all programs and apps as root/admin (even the webserver), therefore I thought Docker would be a solution. Now I have some Docker instances deployed and their processes appear to run also as root/admin. Which makes me think: Is it a false sense of security I have at this moment? Or is using the docker containers much safer than 'regular' root? I assume you are concerned about containerized applications running as root. Root in container is a risk.
Docker Run Command
It still interacts with the kernel as root. And if an application manages to break out of container, it has root privileges on host. Though, root in container has restricted compared to root on host. It does not have capability SYSADMIN that is needed for mount. However, avoid root in container whenever possible to minimize risks. If your containerized applications don't need root privileges, you can run containers with an unprivileged user.
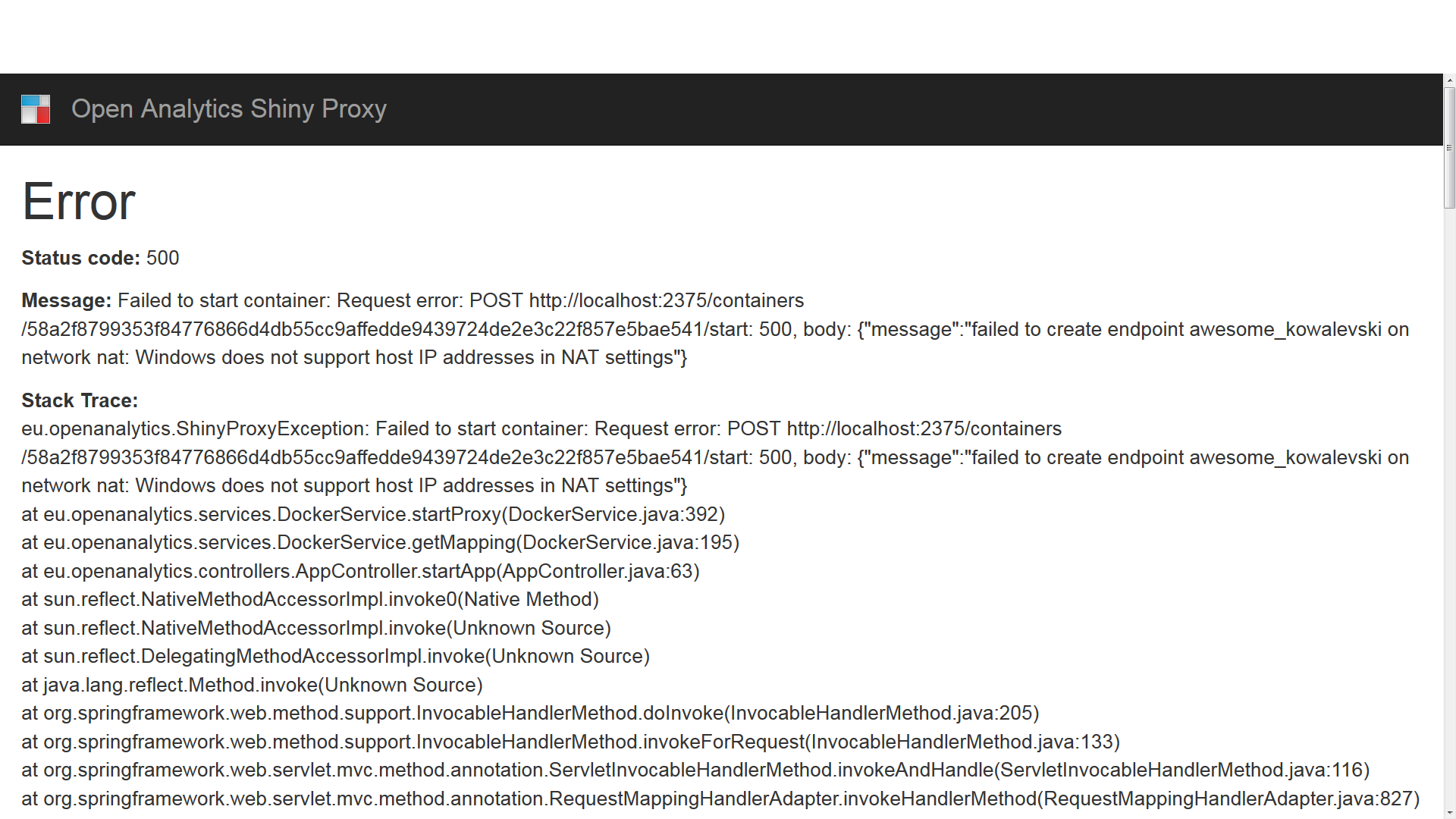
The easiest way is to specify option -user UID:GID in docker run. But I assume you need root privileges for your containerized applications. Docker provides user namespacing to adress this. I do not give an example setup here as I am not really familar with user namespacing. I set it up one time and can confirm it works. I recommend to read the documentation: For short: The user namespace setup accomplishes a 'fake' root user in container that on host is mapped to an unprivileged user. If the application breaks out, it does not have root privileges on host.
Apart from that, you can reduce container capabilities to improve container security. Use option -cap-drop=xyz and drop everything your container does not need. Or even better, use -cap-drop=ALL and add only capabilities that are really needed with e.g. Look at Another option to improve container security is -security-opt=no-new-privileges.